
The D-Link EXO AX4800 (DIR-X4860) router is liable to distant unauthenticated sing execution that will per chance furthermore lead to total instrument takeovers by attackers with glean entry to to the HNAP port.
The D-Link DIR-X4860 router is a excessive-efficiency Wi-Fi 6 router capable of speeds of up to 4800 Mbps and evolved facets appreciate OFDMA, MU-MIMO, and BSS Coloring that enhance effectivity and slice assist interference.
The instrument is particularly accepted in Canada, and or no longer it is provided within the world market in response to D-Link’s net set aside, and composed actively supported by the provider.
Recently, the SSD Staunch Disclosure team of workers of researchers announced that they came upon flaws in DIR-X4860 gadgets working the latest firmware model, DIRX4860A1_FWV1.04B03, which permits unauthenticated distant sing execution (RCE).
“Security vulnerabilities in DIR-X4860 allow distant unauthenticated attackers that can glean entry to the HNAP port to fabricate elevated privileges and whisk instructions as root,” reads SSD’s disclosure.
“By combining an authentication bypass with sing execution the instrument would per chance be fully compromised.”
Having access to the Home Community Administration Protocol (HNAP) port on the D-Link DIR-X4860 router is rather easy in most instances, as or no longer it is always HTTP (port 80) or HTTPS (port 443) accessible via the router’s distant management interface.
Exploitation job
The SSD analysts have shared step-by-step exploitation instructions for the issues they came upon, making a proof-of-opinion (PoC) exploit now publicly obtainable.
The attack begins with a specially crafted HNAP login count on to the router’s management interface, which contains a parameter named ‘PrivateLogin’ discipline to “Username” and a username of “Admin”.
The router responds with a collection aside aside, a cookie, and a public key, and these values are outdated to generate a official login password for the “Admin” tale.
A apply-up login count on with the HNAP_AUTH header and the generated LoginPassword is disbursed to the aim instrument, surely bypassing authentication.
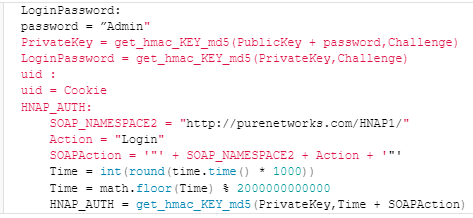
Supply: SSD Staunch Disclosure
With authenticated glean entry to, the attacker then exploits a sing injection vulnerability within the ‘SetVirtualServerSettings’ purpose via a specially crafted count on.
The inclined ‘SetVirtualServerSettings’ purpose processes the ‘LocalIPAddress’ parameter with out moral sanitization, permitting the injected sing to enact within the context of the router’s working system.
SSD says it has contacted D-Link three times to fragment its findings with the router maker over the final 30 days, but all attempts to bid them have been unsuccessful, leaving the issues for the time being unfixed.
BleepingComputer has also reached out to D-Link with a connected count on, and we’re composed looking ahead to a comment.
Except a safety firmware update is made obtainable, users of the DIR-X4860 need to composed disable the instrument’s distant glean entry to management interface to forestall exploitation.

Leave a Reply