
Getty Pictures
As many as 165 customers of cloud storage provider Snowflake bask in been compromised by a team that obtained login credentials by data-stealing malware, researchers mentioned Monday.
On Friday, Lending Tree subsidiary QuoteWizard confirmed it changed into among the many customers notified by Snowflake that it changed into affected in the incident. Lending Tree spokesperson Megan Greuling mentioned the company is in the job of determining whether or now not data saved on Snowflake has been stolen.
“That investigation is ongoing,” she wrote in an electronic mail. “As of this time, it doesn’t seem that user monetary sage data changed into impacted, nor data of the mummy or father entity, Lending Tree.”
Researchers from Mandiant, a Google-owned security firm Snowflake retained to investigate the mass compromise, mentioned Monday that the companies bask in to this level recognized 165 customers whose data can bask in been stolen in the spree. Stay Nation confirmed 10 days ago that data its TicketMaster team saved on Snowflake had been stolen following a posting offering the sale of the total names, addresses, phone numbers, and partial bank card numbers for 560 million Ticketmaster customers.
Santander, Spain’s ideal bank, mentioned now not too long ago that data belonging to about a of its customers has also been stolen. The identical team advertising the Ticketmaster data provided the sale of Santander data. Researchers from security firm Hudson Rock mentioned that stolen data changed into also saved on Snowflake. Santander has neither confirmed nor denied the claim.
Mandiant’s Monday post mentioned that every the compromises it has tracked to this level bask in been the of login credentials for Snowflake accounts being stolen by infostealer malware and saved in extensive logs, as soon as in a while for years at a time. No longer one among the affected accounts made exhaust of multifactor authentication, which requires customers to manufacture a one-time password or extra methodology of authentication moreover a password.
The team finishing up the assaults is financially motivated, with contributors largely located in North The usa. Mandiant is monitoring it as UNC5537. Company researchers wrote:
In step with our investigations to this level, UNC5537 obtained salvage entry to to a couple of organizations’ Snowflake buyer instances by stolen buyer credentials. These credentials bask in been basically obtained from a couple of infostealer malware campaigns that infected non-Snowflake owned programs. This allowed the menace actor to manufacture salvage entry to to the affected buyer accounts and led to the export of a prime volume of buyer data from the respective Snowflake buyer instances. The menace actor has which potential that reality begun to extort a good deal of the victims at as soon as and is actively attempting to sell the stolen buyer data on recognized cybercriminal boards.
Mandiant recognized that nearly the general credentials worn by UNC5537 bask in been on hand from historical infostealer infections, some of which dated as a long way motivate as 2020.
The menace campaign conducted by UNC5537 has resulted in a colossal change of winning compromises because of about a most main factors:
- The impacted accounts weren’t configured with multi-ingredient authentication enabled, meaning winning authentication most efficient required a sound username and password.
- Credentials recognized in infostealer malware output bask in been nonetheless legitimate, in some instances years after they bask in been stolen, and had now not been circled or updated.
- The impacted Snowflake buyer instances did now not bask in network allow lists in train to most efficient allow salvage entry to from depended on locations.
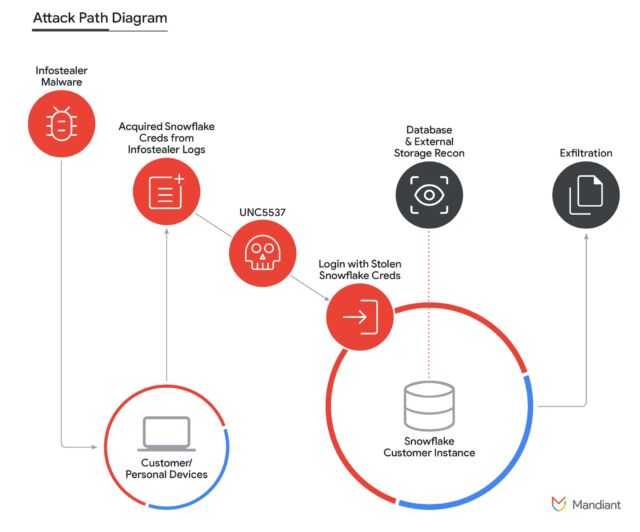
Amplify / Assault Course UNC5537 has worn in assaults against as many as 165 Snowflake customers.
Mandiant
Preliminary salvage entry to to affected Snowflake accounts continuously occurred with the usage of the company’s native SnowSight or SnowSQL, that are a web-basically basically based user interface and a uncover-line interface respectively. The menace actors also worn a personalised utility that reveals up as “rapeflake” in logs and that Mandiant tracks as FrostBite.

Leave a Reply